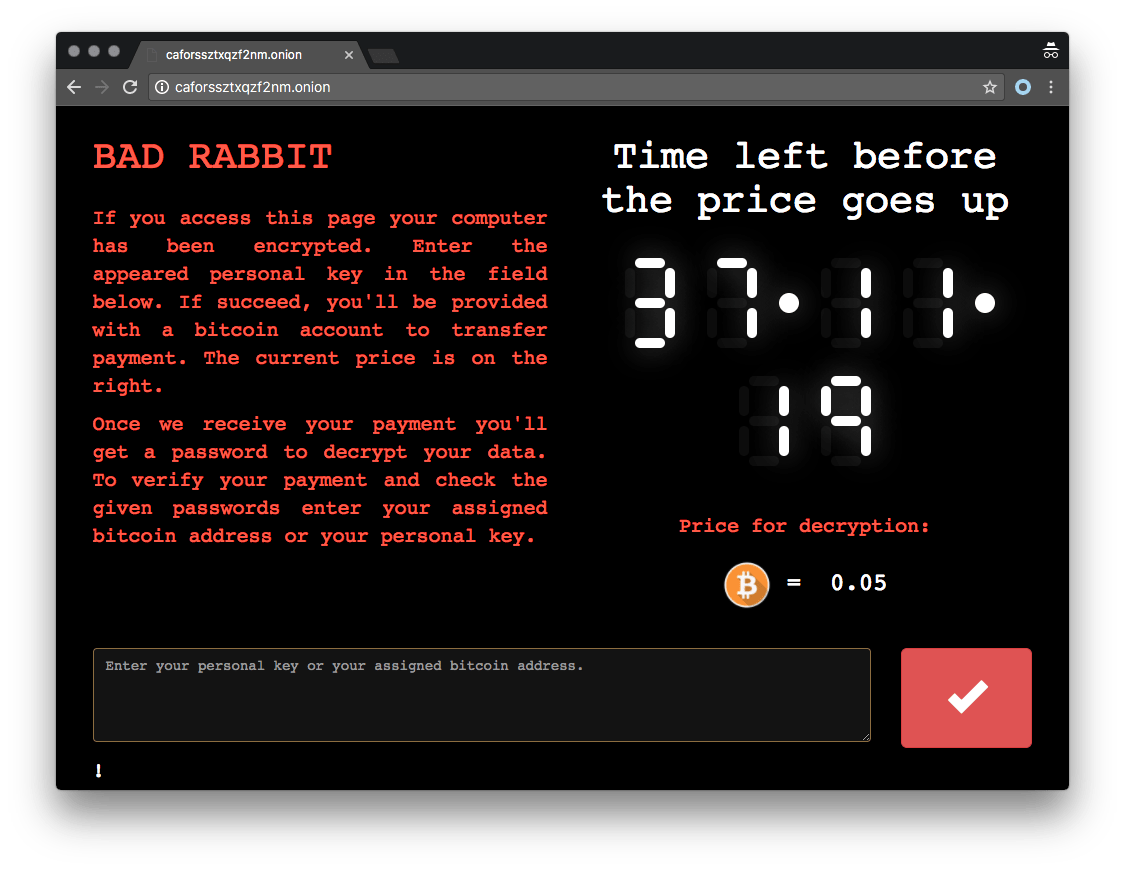
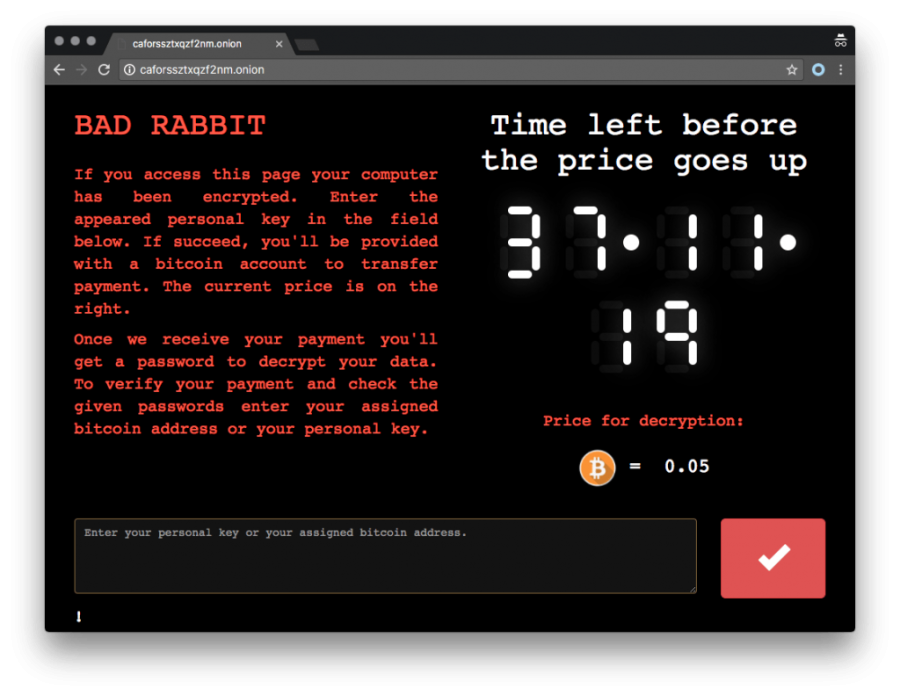
The Judiciary Police (PJ) have urged the public to be aware of a new ransomware attack known as “Bad Rabbit”.
According to recent overseas media reports, “Bad Rabbit” uses a similar attacking method of another malware known as “Peyta”. “Bad Rabbit” is disguised as an Adobe Flash installer. It appears as a file asking users to update the software. However, once the file is opened it encrypts the files of the infected computer. The ransom note and payment page demands around US$280 (MOP2,250) in Bitcoins for the decryption key with a 40-hour deadline for payments.
Earlier this month, “Bad Rabbit” attacked a number of Russian media websites, a Ukrainian airport and the subway system in Kiev, the capital of Ukraine. According to Kaspersky Lab specialist Vyacheslav Zakorzhevsky, attacks were also found in countries including Turkey and Germany.
Kaspersky Lab described “Bad Rabbit” on its official “Daily” website on October 24 as a “new ransomware epidemic on the rise.”
According to company’s findings, “Bad Rabbit” is a drive-by attack – victims download a fake Adobe Flash installer from infected websites and manually launch the .exe file, thus infecting themselves.
According to the Macau Post Daily, last month, a school in Macau was attacked by the ransomware “Petya”, affecting five computers in that school, according to the Judiciary Police at that time.
The Judiciary Police said in Sunday’s warning they had not received any local reports about “Bad Rabbit” so far. Meanwhile, the warning asked the public to pay attention to files related to an Adobe Flash update as they could be a bogus one for ransom. According to the PJ statement, users should also have a sense of cyber security, update their antivirus software as it could detect and stop “Bad Rabbit”, and not open any files from unreliable sources.